How do Public and Private keys work?
Let's understand asymmetric encryption in Blockchain
Table of contents
No headings in the article.
Before we dive deep into the Encryption Decryption process. Let's get started with: How do Bitcoin Wallets work?
As we know, to use a cryptocurrency, we need a wallet such as MetaMask to store our virtual coins. And every wallet has a unique address. You can consider it equivalent to a bank account number which is unique to everyone.
So how are these actually calculated? Are these randomly generated strings of letters or numbers?
Umm.. Actually, there is a bit of logic behind it. Anyone can create a new wallet by generating a public and private key pair with a certain algorithm. If you've ever set up a Metamask or any other wallet for that matter you would know that it's fairly easy to do it that's cause all the algorithm work is done for you by the wallet itself.
In the case of Bitcoin or Ethereum that is via an Elliptical curve digital signature algorithm. That's quite a mouthful, but the takeaway here is that the algorithm will spit out a private key and a public key.
These keys are mathematically linked to each other. We can take the private key and derive the public key from it. But we cannot take the public key and turn it into the private one which ensures safety for our wallets. And this phenomenon is related to Asymmetric encryption.
To understand Asymmetric Encryption lets under Symmetric Encryption first:
Supposed Dan wanted to send a document to Bob. So before sending the document, Dan encrypted it with a lock.
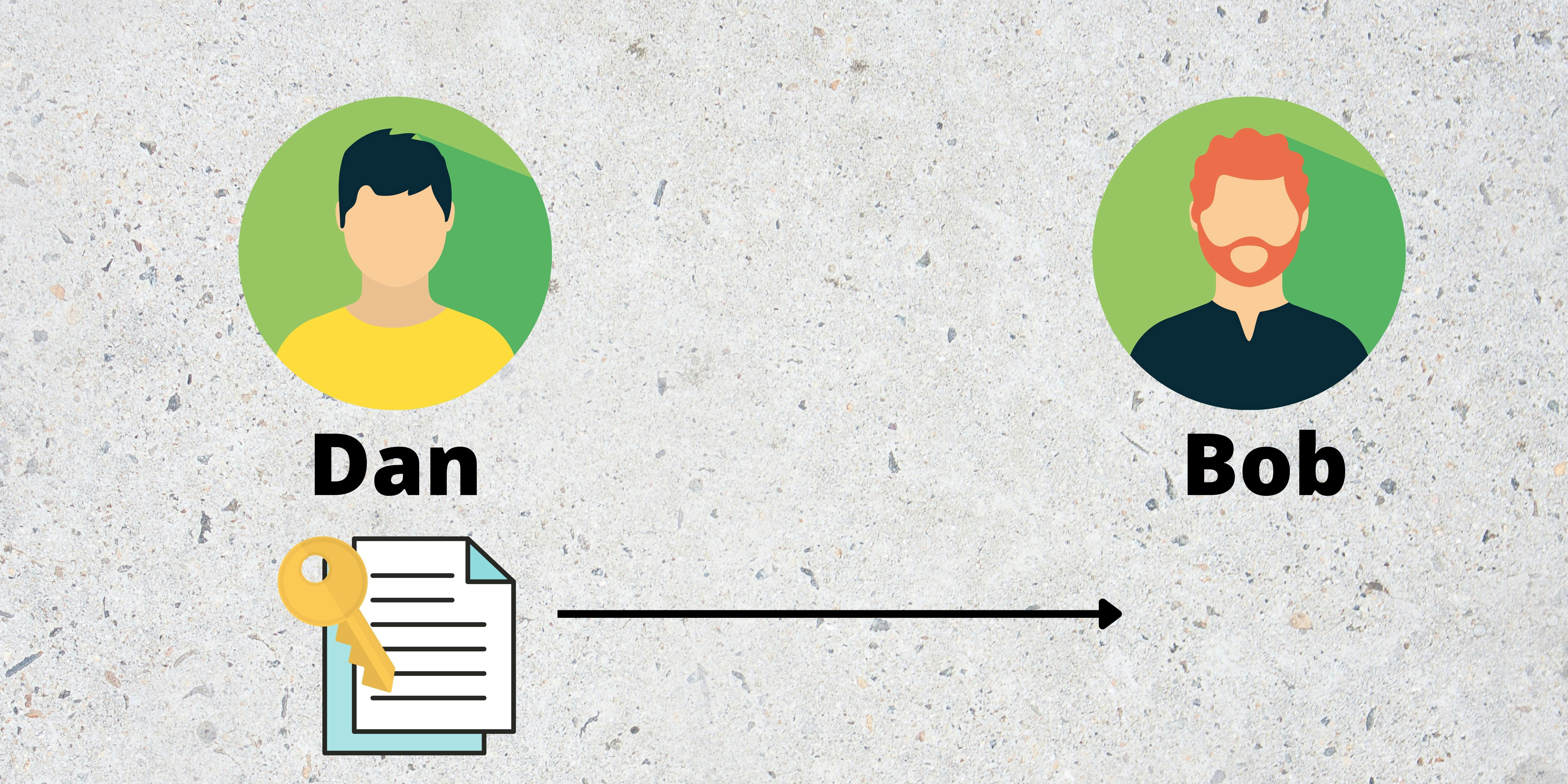 After encryption, Dan sends it to Bob.
Now if Bob wanted to decrypt it, he needed the key to open the lock.
After encryption, Dan sends it to Bob.
Now if Bob wanted to decrypt it, he needed the key to open the lock.
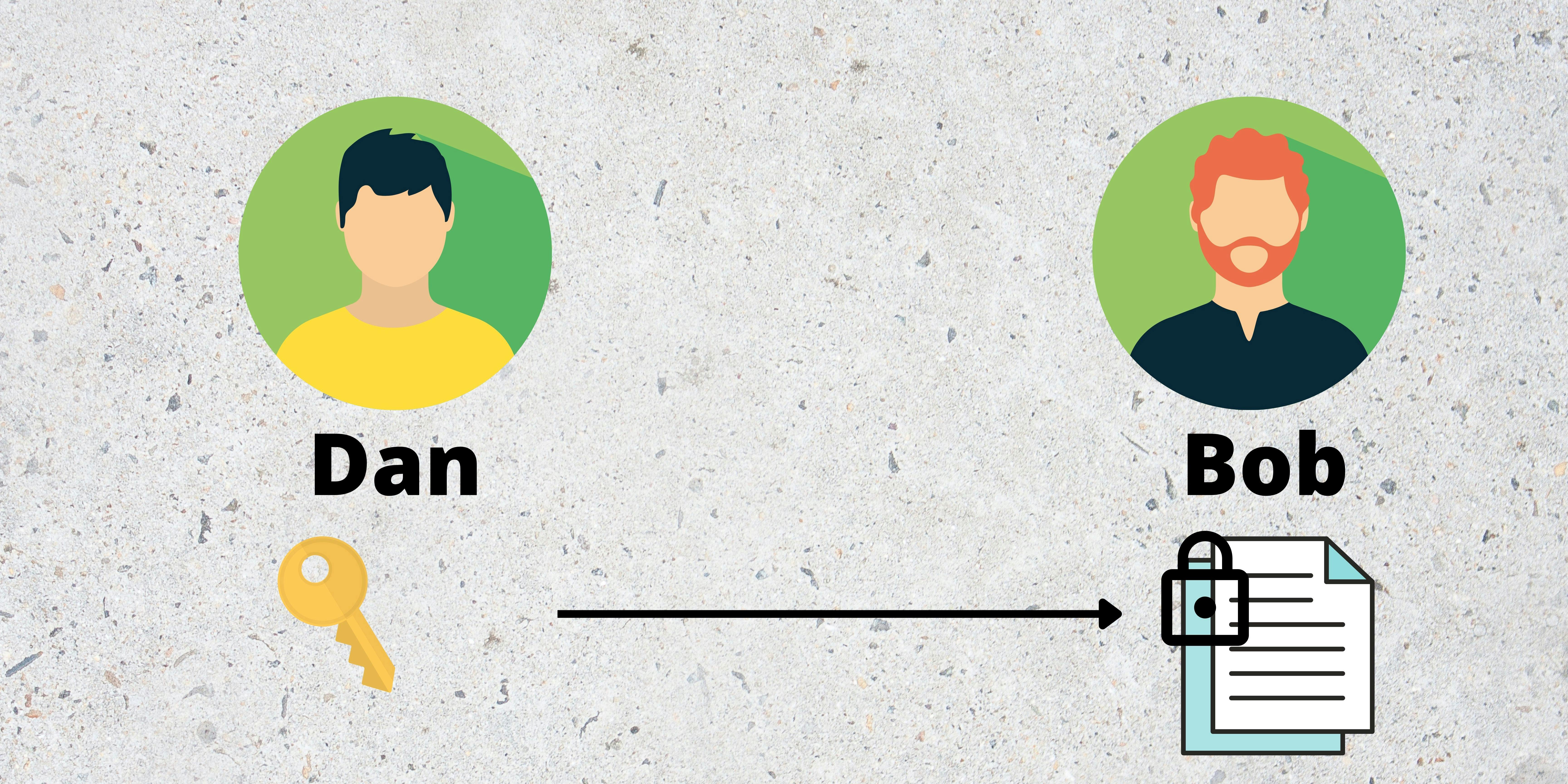
Now comes the real deal. How does Dan share this key or password securely with Bob? If Dan sends it through email, there is a possibility that others might interfere and use it to decrypt the document.
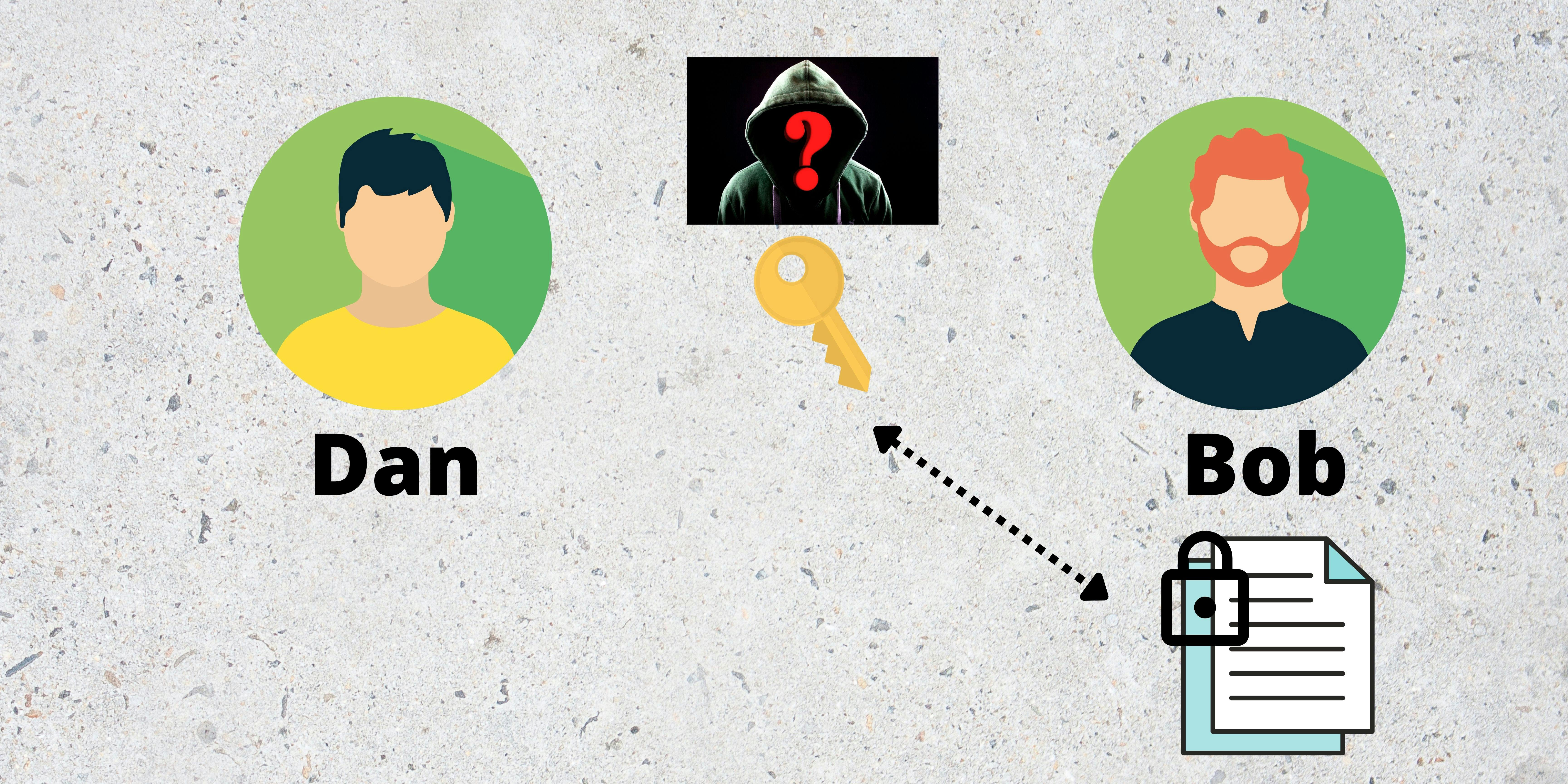
This is where the symmetric encryption fails and Asymmetric Encryption takes the lead.
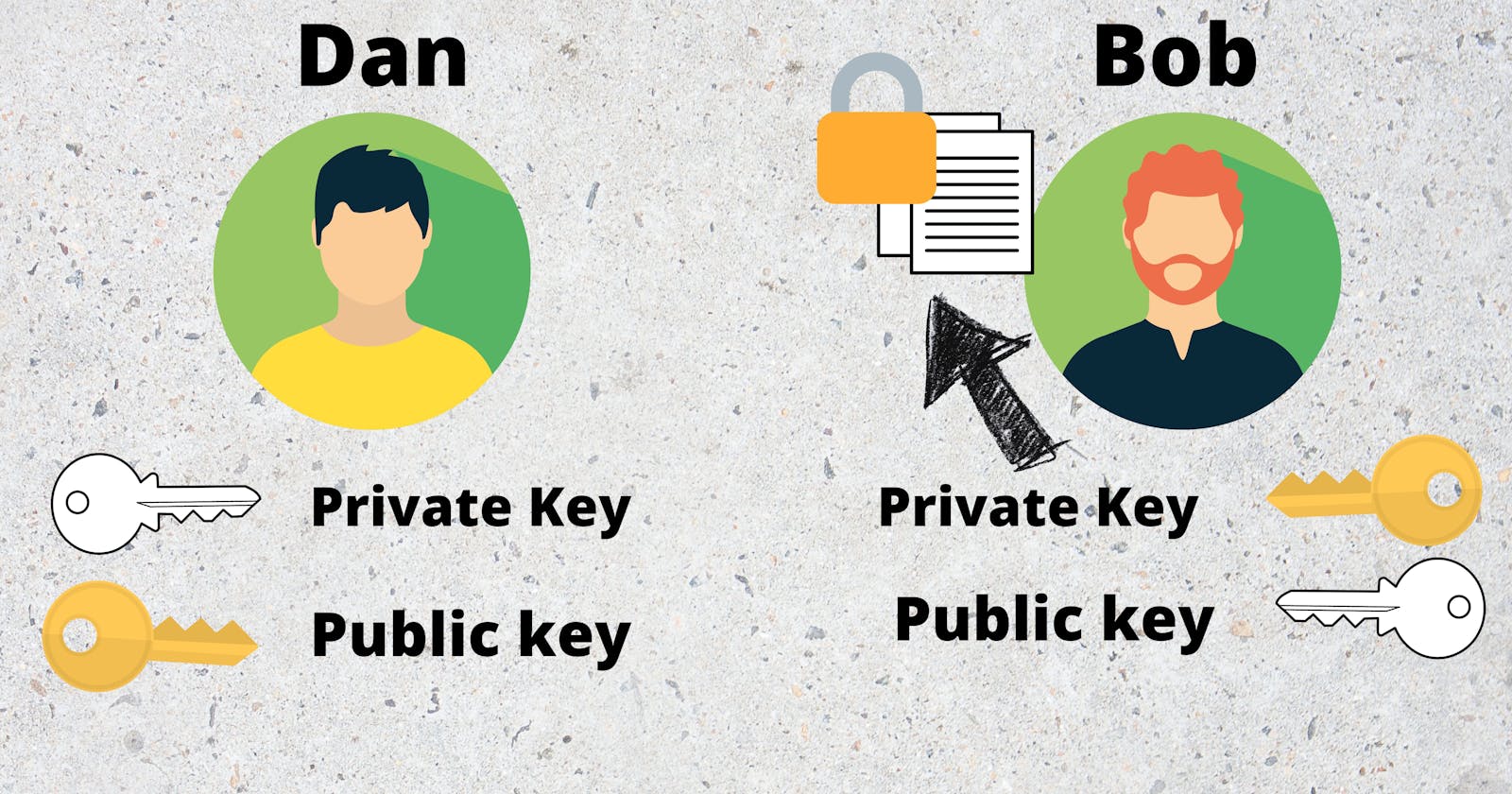
In Asymmetric encryption. Dan and Bob- Both will have their own set of private and public keys.
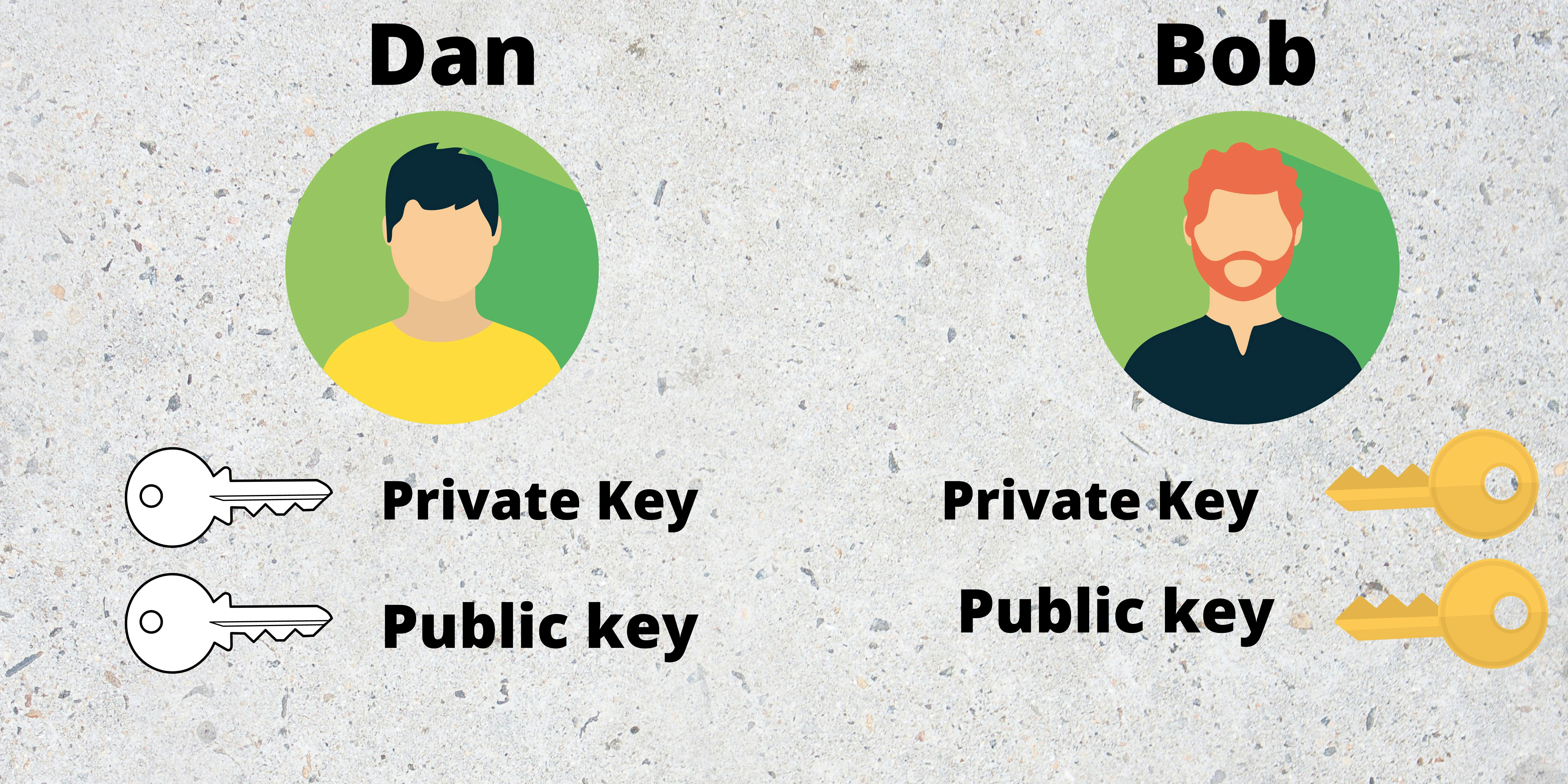
If Dan wanted to send something to Bob, they will exchange their public keys.
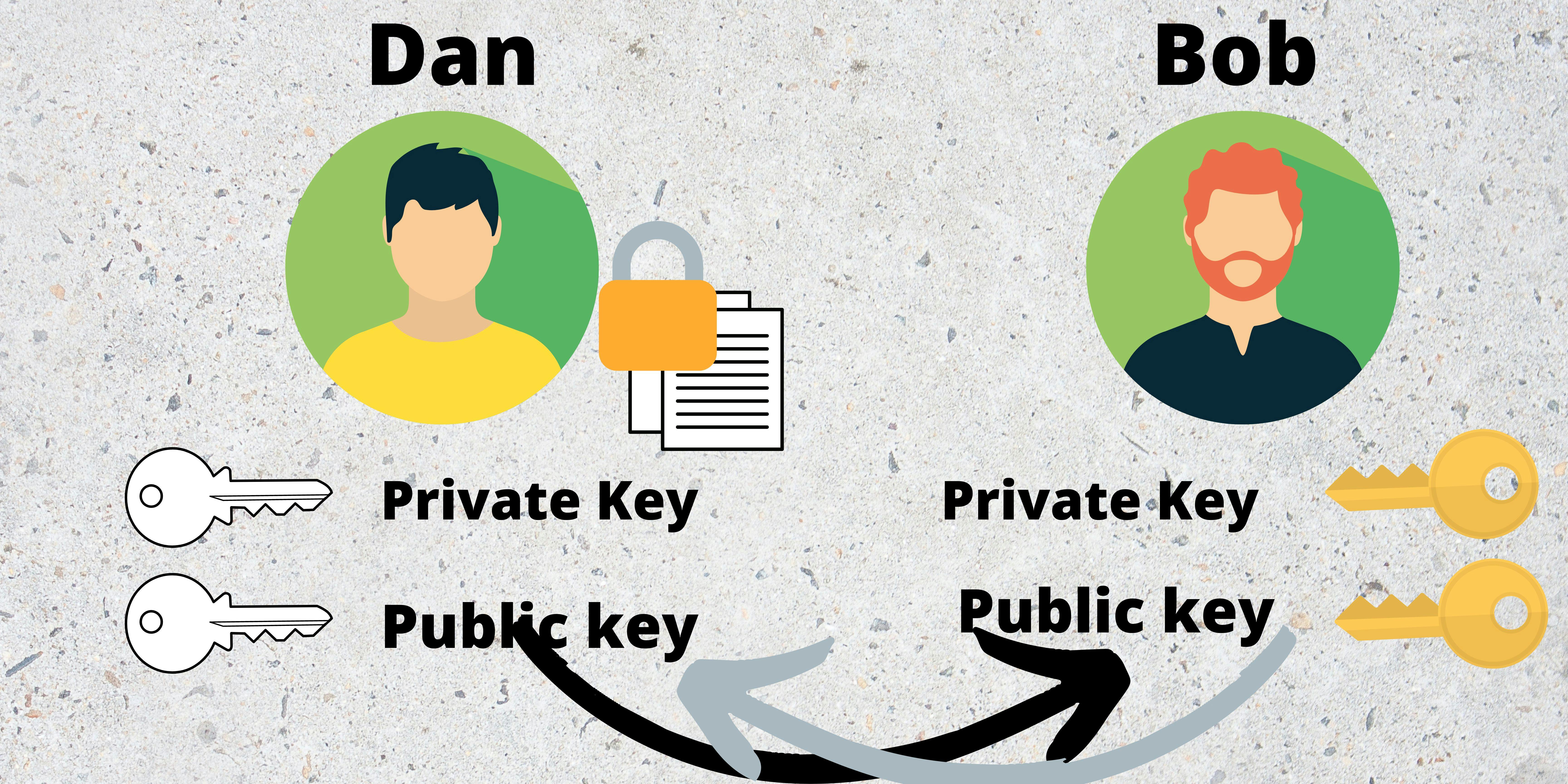
Dan will Encrypt the data using Bob's Public key which can only be decrypted using Bob's private key.
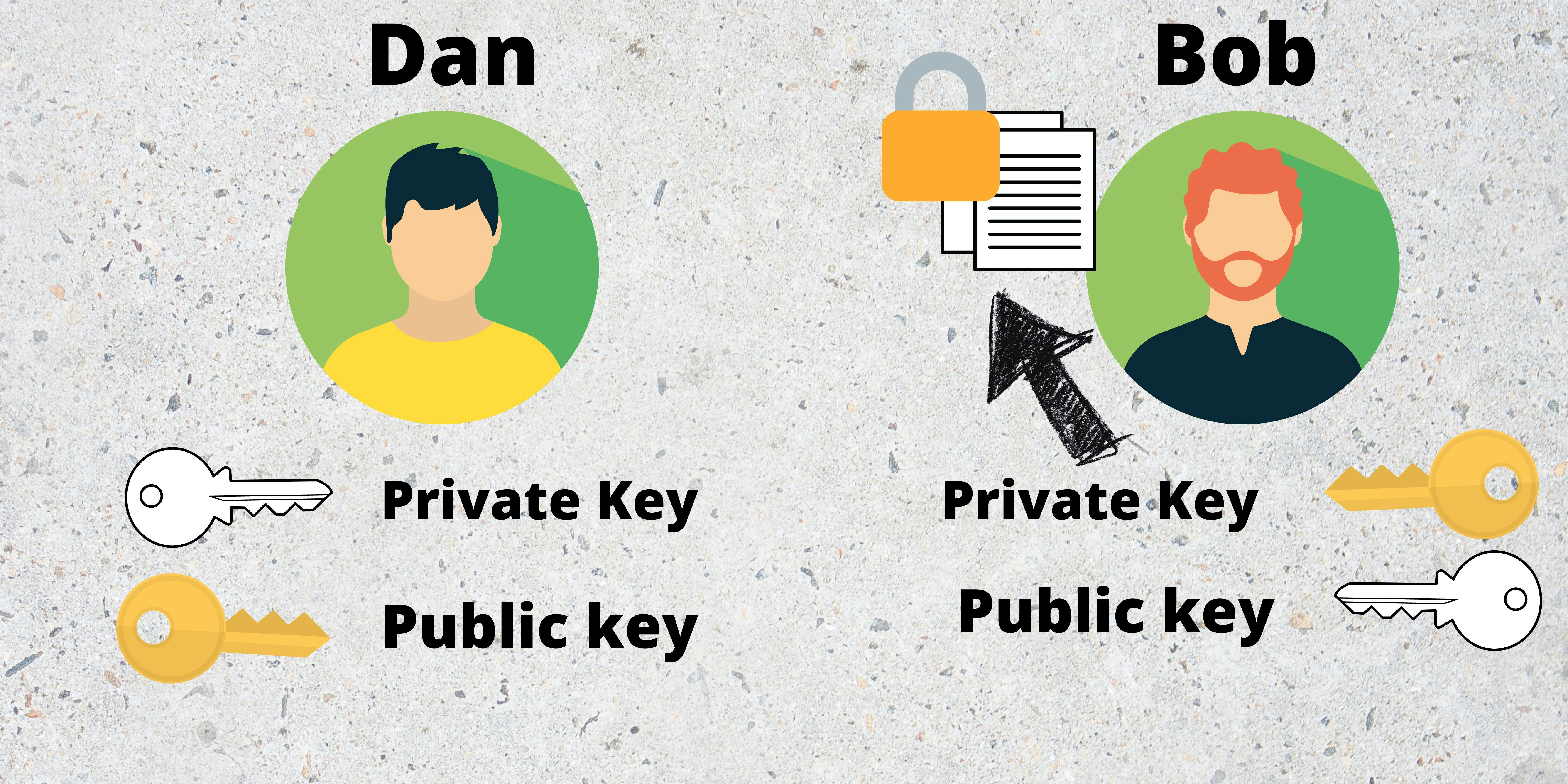
After encryption, even Dan can't decrypt it without Bob's private key.
If an attacker finds out Dan's private key, they'll have the power to decrypt all documents sent to Dan. However, they'll still be not able to decrypt the documents sent out by Dan.
This Asymmetric encryption is not just used in Bitcoin but also by HTTPS websites(SSL).
I hope, I made the explanation simple. See you in the next one.